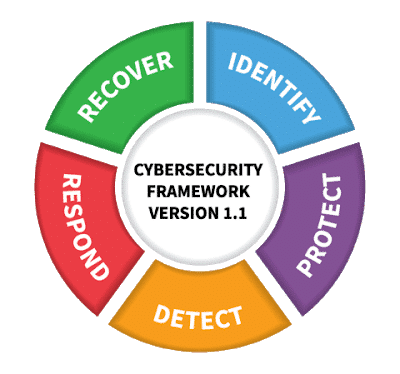
 Cybersecurity is a complicated subject. It’s hard to understand all the facets, the moving gears that are constantly changing. It’s complicated even for me and I work with it everyday. There are aspects that can help to make sense of the fundamentals. The 5 key steps within the framework that the National Institute of Standards and Technology (NIST) lays out are Identify, Protect, Detect, Respond, and Recover.
Identify
The Identify pillar functions to develop an awareness to the key aspects of a cybersecurity plan. This includes knowing how security fits in in the context of your business, risk management and how a cyber attack can affect the future operations of your business, and what assets require which specific resources and protections.
Examples of actions within this pillar include:
Cybersecurity is a complicated subject. It’s hard to understand all the facets, the moving gears that are constantly changing. It’s complicated even for me and I work with it everyday. There are aspects that can help to make sense of the fundamentals. The 5 key steps within the framework that the National Institute of Standards and Technology (NIST) lays out are Identify, Protect, Detect, Respond, and Recover.
Identify
The Identify pillar functions to develop an awareness to the key aspects of a cybersecurity plan. This includes knowing how security fits in in the context of your business, risk management and how a cyber attack can affect the future operations of your business, and what assets require which specific resources and protections.
Examples of actions within this pillar include:
- Identifying physical and software assets (servers, workstations, financial applications, personal data) within your business to create and maintain an asset management program.
- Identifying vulnerabilities within those assets like personal information, threats to business resources, and risk response activities as a basis for your risk assessment
- Creating a risk management strategy for your company, establishing how much risk you’re willing to take.
Protect
The protect pillar outlines appropriate steps to ensure that critical infrastructure services are in place.(Dark Web Scans, Advanced Endpoint Protection, Backup and Disaster Recovery, etc). This allows you to limit or contain the damage in the event that a cyber attack occurs. Examples of actions within this pillar include:- Providing your staff with knowledge through awareness and training.
- Providing data protection aligned with your business’ risk strategy to protect the confidentiality, integrity, and availability of information, also known as encryption.
- Implementing processes to maintain and manage the safety of your assets.
- Protecting business resources through remote monitoring and maintenance (RMM).
- Managing protective technology to ensure the security and resilience of systems and assets are consistent with your policies, procedures, and agreements.
Detect
 The Detect pillar serves to define the activities to identify the occurrence of a cybersecurity event and enables timely discovery of cybersecurity events.
Examples of actions within this pillar include:
The Detect pillar serves to define the activities to identify the occurrence of a cybersecurity event and enables timely discovery of cybersecurity events.
Examples of actions within this pillar include:
- Ensuring that events are detected, and their potential impact is understood.
- Implementing monitoring capabilities to scan cybersecurity events and verify the effectiveness of protective measures including network and physical activities.
- Maintaining detection processes to provide awareness of events.
Response
The respond pillar includes steps to take action regarding a known cybersecurity event. The respond pillar lends the ability to minimize the impact of a potential cybersecurity threat. Examples of actions within this pillar include:- Ensuring response planning processes are executed during and after an incident.
- Communicating during and after an event with stakeholders, law enforcement, employees, and clients.
- In-depth analysis is conducted to ensure effective response and recovery activities including forensic analysis, and determining the severity of the attack.
- Actions are taken to prevent the possible spread of the attack.
- Enhancing future protections by learning from past events.
Recover
The Recover pillar serves to create a plan to revert changed services and impacted items. This plan allows for timely recovery of operations and reduced impact- both cost and productivity- from a cybersecurity event. Examples of actions within this pillar include:- Ensuring your business implements recovery planning processes and procedures to restore systems and assets affected by cybersecurity events.
- Improve recovery efforts based on previous cyber attacks.
- Provide updates both internally and externally to all those affected throughout the duration of the cybersecurity incident.
 Having a proactive and holistic cybersecurity plan can be the difference between being in business tomorrow or not. The cost of suffering from a cyber attack with no protection far surpasses the cost to have these 5 pillars in place. Still have questions? Want to know how to protect your business? Email us at sales@baroan.com, or call at (201) 796-0404 and ask for Guy or Ari.
Having a proactive and holistic cybersecurity plan can be the difference between being in business tomorrow or not. The cost of suffering from a cyber attack with no protection far surpasses the cost to have these 5 pillars in place. Still have questions? Want to know how to protect your business? Email us at sales@baroan.com, or call at (201) 796-0404 and ask for Guy or Ari.

Information Technology Aligned With Your Business Goals?
Baroan is a complete IT services & IT support company working with organizations in Elmwood Park and across the United States of America.
When it comes to IT services and solutions, you need someone who not only comprehends the IT industry but is also passionate about helping clients achieve long-term growth using proven IT solutions. Guy, in leading our company, is committed to helping clients improve their technology in order to develop a competitive edge in their industries.
At Baroan Technologies, Guy Baroan leads a team of dedicated professionals who are committed to delivering exceptional IT services and solutions. With his extensive expertise and hands-on experience, Guy ensures that clients receive the utmost support and guidance in their IT endeavors. Trust in Baroan Technologies to elevate your business systems and stay ahead in today’s competitive landscape.



